As development teams grow and infrastructure becomes more distributed, the way developers access critical systems has changed dramatically. Gone are the days when a handful of developers accessed a single on-prem server with a simple SSH key. Today’s engineers often juggle multiple Kubernetes clusters, a range of databases (SQL, NoSQL, and everything in between), and a sprawl of cloud-based services—each with its own requirements for credentials, permissions, and policies.
This complexity has introduced new friction points for developers. On one hand, there’s a strong push for agility: teams need quick, secure access to their tools and environments. On the other, stricter compliance mandates and an evolving threat landscape require more granular controls, better visibility, and airtight audit trails. Balancing these forces can feel like threading a needle in a high-stakes environment.
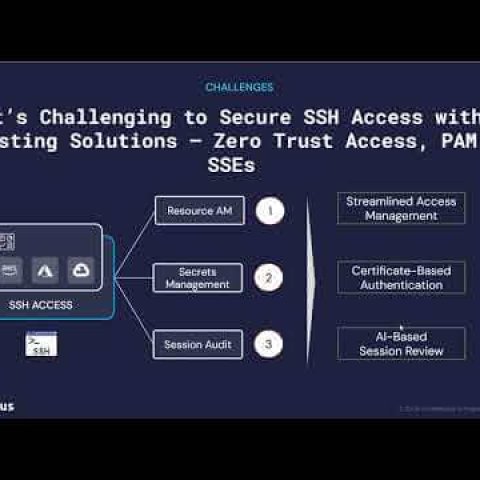
In this post, we’ll break down three major challenges developers face when accessing the critical infrastructure that powers modern applications—complexity of access management, credential sprawl, and lack of consolidated audit—and explore strategies to tackle them head-on.
1. The Complexity of Access Management
Developers work with a broad set of resources: SSH into various servers, manage containers in Kubernetes, query multiple databases, and integrate third-party APIs. Each of these services may have its own unique authentication scheme and access policies. The result is an intricate web of credentials, user directories, VPNs, bastion hosts, and role-based permissions. When a developer needs access to a new environment or when someone leaves the company, updating and coordinating all these permissions can become a manual, error-prone, and time-consuming process.
Lumeus offers Enterprise Identity and Access Management integrations out of the box, with a robust policy engine that enables least privileged access with Just-in-Time (JIT) access. In addition, Lumeus enhances connectivity, this allows for the elimination of publicly facing resources.
2. Credential Sprawl
It’s not uncommon for developers to store credentials in multiple places—environment variables, configuration files, password managers, or even shared documents—and these credentials can multiply quickly. Managing a labyrinth of secrets is both a security and productivity challenge. If a single SSH key or database password leaks, it could open the door to unauthorized access. If developers waste time hunting down credentials in multiple systems, productivity suffers.
When speaking to customers, we often hear the following issues:
- Inconsistent Storage Locations: Credentials hidden in code repositories, shared folders, or personal vaults.
- Rotation and Revocation Issues: Stale credentials remain active, or rotating keys is a tedious process.
- Lack of Visibility: Without a clear map of who holds what keys, audit and compliance become a nightmare.
Lumeus eliminates credential sprawl and dependency on vaults by natively supporting certificate-based authentication. SSH Keys and Database credentials are substituted by short lived certificates; this methodology increases security posture, especially if combined with JIT access.
3. Lack of Consolidated Audit
When access information is scattered across multiple tools—SSH logs, database audit trails, Kubernetes admission controllers—gaining a single, unified view of who did what, when, and where can be challenging. Without consolidated audit data, it’s difficult to hold teams accountable, investigate potential incidents efficiently, or prove compliance during security audits.
Lumeus automatically logs every session (command transcription and human-readable description of the session), provides SSH session capture (and replay), transcribes queries and automatically detects and classifies sensitive information like personal, payment or health data.
Demos
Watch this playlist that showcases 3-minute demos for Secure SSH, Database and Kubernetes Access.