According to the Zscaler ThreatLabz 2024 VPN Risk Report, over half of surveyed organizations—56%—experienced one or more VPN-related cyberattacks in the last year, an alarming jump from 45% the year before. These rising attacks underscore how legacy remote access methods, particularly VPNs, often fail to keep pace with modern threats and distributed workforces. As a result, more and more organizations are turning to Zero-Trust models that actively verify each user, device, and transaction before granting access.
In this blog, we’ll take a closer look at the emerging concept of Remote Privileged Access Management (RPAM) and why it has become a pillar for Zero-Trust adoption. By defining RPAM use cases we’ll highlight how Lumeus builds on RPAM principles to deliver ephemeral, policy-driven access without relying on VPN tunnels or static credentials.
What is Remote PAM?
According to Gartner the RPAM use case “ is focused on supporting remote IT external staff and providing a secure VPN-less approach for performing remote privileged tasks. Such tasks include session-brokering and time-bound, session-specific, JIT access. RPAM is also critical for improving identity lifecycle management (LCM) for remote privileged users, especially for short-term access, which requires a specific set of policies and procedures to guide the creation and assignment of privileges and access expiration.” (1)
The Need for RPAM
As IT ecosystems and DevOps processes become more dynamic, privileged access requirements shift rapidly. Short-term consultants, third-party vendors, or even AI-based workflows might need to troubleshoot a production environment or push a hotfix on short notice. Traditional approaches—like distributing permanent SSH keys, rolling out company-wide VPN accounts, or embedding long-lived credentials in code—lead to overexposure and credential sprawl. Once handed out, these static keys or VPN credentials are difficult to track and even harder to revoke, creating dangerous blind spots for security teams.
RPAM Pillars:
- Granular Control: Restrict access to specific machines, databases, web applications, or AI services rather than granting blanket privileges across entire networks.
- Just-in-Time (JIT) Access: Dynamically provide privileges only for the exact duration needed, automatically revoking them afterward.
- VPN-Less Connectivity: Eliminate broad network tunnels that expand the attack surface, aligning with Zero-Trust security principles.
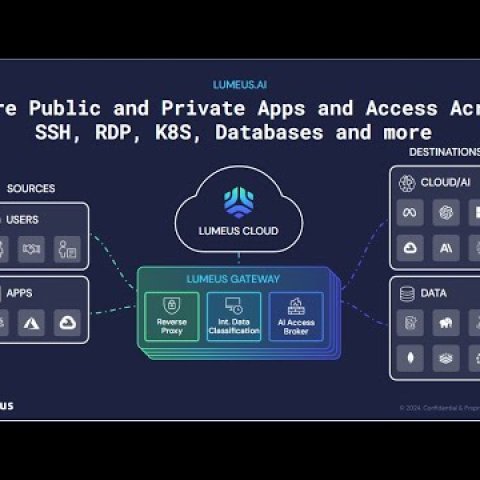
Lumeus’ RPAM Capabilities
The Lumeus platform is designed to satisfy Remote PAM with capabilities like:
- Enterprise Identity and Access: Lumeus integrates with IAM solutions out of the box, regardless of the flavor (Microsoft, Okta, Google and others), this provides a seamless experience using enterprise single sign-on and multi-factor authentication.
- Policy Rules: Lumeus’ rules engine is robust enough to support multiple identity sources, diverse use cases and controls such as JIT, data protection or AI monitoring.
- Secure SSH Sessions: Developers or contractors can request short-lived certificates for granular command-line access. No lingering SSH keys remain, drastically reducing the threat of leaked or orphaned credentials.
- Database Access: External DBAs, data analysts, or AI routines can get time-bound privileges to specific schemas or tables, granting them autonomy without opening the entire database. Detailed query-level logs ensure accountability and compliance.
- Kubernetes Access: As container orchestration drives modern apps, ephemeral certificates can limit user scope to specific namespaces or pods, preventing lateral movement and enforcing fine-grained governance over microservices.
- Private Web Application Access: External stakeholders, such as support teams or contractors, often need secure access to internal web portals or application dashboards. With RPAM, they can be granted session-based access to private web apps—without spinning up a full-scale VPN. Once their session ends, the gateway automatically severs and revokes privileges, ensuring no lingering access paths remain.
- Emerging AI App Use Cases: From AI-driven analytics to predictive maintenance tools, machine learning workflows require privileged access to data repositories. The challenge is to implement proper governance, visibility, data protection and privacy while enabling productivity in this modern use case.
What is the Lumeus Difference?
Design Principles – Zero Trust and AI
Lumeus was designed from the ground up to be a Zero Trust Access solution powered by AI. Out of the box, with IAM integration and a robust policy engine, it can tackle the granular control and JIT needs of RPAM.
The other key advantage is flexible connectivity. Lumeus offers Client-Based Access for advanced or technical users who need a deep level of functionality—think developers troubleshooting a server or DevOps engineers managing Kubernetes clusters—Lumeus provides a lightweight client that securely handles authentication and access controls.
For less technical users or for scenarios where installing additional software isn’t ideal—say, a temporary contractor working on their personal device—Lumeus offers a fully clientless, browser-based access option. Through a secure web portal, users can be granted just-in-time credentials to access protected apps, SSH sessions, or critical SaaS platforms. With single sign-on (SSO) and strong authentication built in, this approach removes the need for VPNs or custom configurations. It’s especially valuable when rapid onboarding or emergency support are at play, allowing teams to adapt quickly without manual setup.
Deep Visibility and Auditing at Every Level
Lumeus provides unmatched transparency into remote privileged activity:
- Command-Level Visibility: SSH sessions are fully recorded at the command level, supporting forensic investigations, compliance audits, and detailed troubleshooting.
- Query-Level Insight: Every database query is captured, enabling security teams to see exactly what data was accessed and when. This granularity is essential for ensuring proper data governance.
- Automatic Data Classification: Sensitive data, be it personal identifiers, health or payment information, is automatically detected and classified. Administrators can then enforce policies around masking or restricting access to ensure compliance and reduce exposure.
By consolidating this visibility and enforcing policy rules, Lumeus allows security teams to maintain full oversight without hindering the developer experience. This balance of security and productivity is vital as organizations strive to release features quickly, adopt DevOps best practices, and remain competitive in a cloud-driven marketplace.
A Single Platform for RPAM needs
In an environment where traditional perimeters have dissolved and development teams span time zones and organizations, Lumeus provides a unified solution. No more juggling static SSH keys, juggling disparate VPN configurations, or leaving databases open to broad privileges. Instead, you gain a dynamic, policy-driven, and fully auditable platform that delivers the best of RPAM: secure, ephemeral, and context-aware access to every critical layer of your stack.
Lumeus ensures you can innovate fearlessly while keeping your organization’s most critical assets safe and compliant.
(1) 2024 Critical Capabilities for Privileged Access Management. Authors: Paul Mezzera, Abhyuday Data, Michael Kelley, Nayara Sangiorgio, Felix Gaehtgens